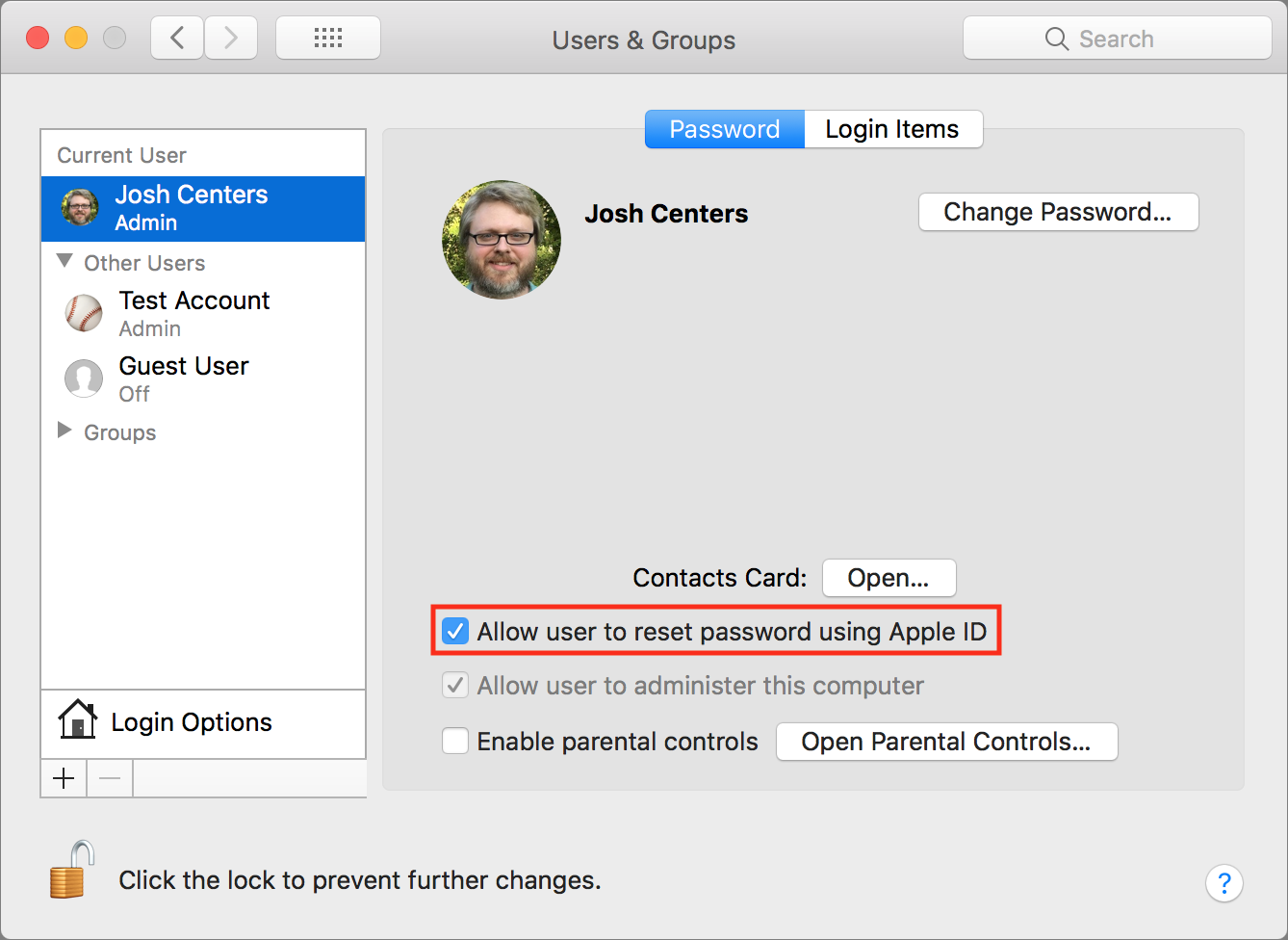
The passwords for all accounts on macOS Mojave 10.14, macOS Sierra, OSX 10.11 El Capitan, OSX 10.10 Yosemite, OSX 10.9 Mavericks and OSX 10.8 Mountain Lion including admin and standard user accounts can be reset and changed when booted from the Recovery Partition on macOS.
- If the account was created at the GUI level or at the command line using 'sysadminctl', and was created as an admin account, then it most definitely has a Secure Token set. Followup #2: Not all Macs will have the SecureToken enabled on all accounts, this is usually the case where the Mac originally came with some version of Mac OS prior to.
- 6: On the right side of the Users & Groups panel, you can click the 'Change Password' button to change a new password for the administrator. 7: Type the new password and verify it. Then fill in the Password hint fields. Click 'Change Password' tab to save these changes. Thus, you can log into the administrator account with this new password.
Boot into Recovery Partition
Reboot into the Recovery Drive by choosing the ‘Apple‘ menu > Restart, hold down the ‘command' + ‘r' keys on the keyboard during the start up process, when you see the start up screen you can let go. When the machine boots eventually you will see the macOS or OS X Utilities screen.
Change an Admin Password in Mac OS X Single User Mode This is a multistep process but it's easy to follow: First you need to enter Single User Mode. Reboot the Mac and hold down Command+S at boot to enter into the command line. You'll see a note where Mac OS X tells you that you need to run two commands in.
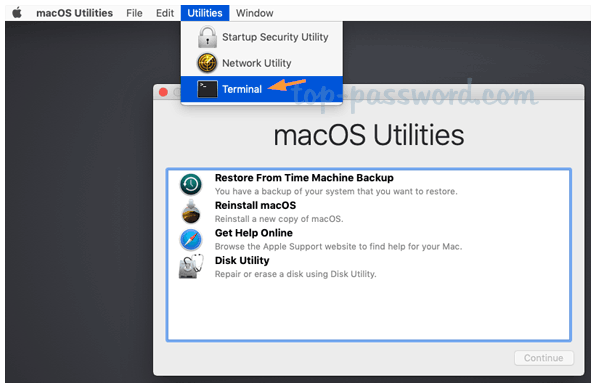
Go to the Utilites menu and select Terminal
At the prompt type ‘resetpassword' (hit enter)
This launches the Reset Password screen, select the Volume Hard Drive in the top part of the window pane, then for the user that you need to reset select the user account in the lower part then add and confirm the new password and click save, you get a confirmation screen and details about the keychain account.
Go to the Apple Menu and click Restart to boot back to the normal hard drive and the new password will take effect immediately.
If you are using macOS Mojave the screen you see is a little friendlier, just select the account you want to reset the password on and follow the instructions.
macOS 10.13 brings changes to sysadminctl. You know those dscl scripts we used to use to create users? No longer supposed to be necessary (luckily they do still work). Now you can create a user with a one-liner, and do other forms of user management, such as enabling FileVault for a given user, or managing the guest accounts. However, you can't do these tasks as root or via sudo. You have to do so with other admin accounts per Apple kbase HT208171 (in fact, this article has been in my queue waiting for that issue to be fixed – but keep in mind I'm not prefacing these with sudo in the below commands). In the below command, we'll pass the -addUser option and then use -fullName to fill in the displayed name of the user, -password to send a password to the account and -hint so we can get a password hint into that attribute:Apple Default Admin Password
sysadminctl -addUser krypted2 -fullName 'Charles Edge' -password testinguser -hint hi
The result would be as follows:
No clear text password or interactive option was specified (adduser, change/reset password will not allow user to use FDE) !
Creating user record…
Assigning UID: 503
Creating home directory at /Users/krypted2Notice that in the above, the system automatically selected a home directory and UID. We could have passed those as well, using Now let's use dscl to view the user we just created:
Macos Default Admin Password Unlocker
dscl . -read /Users/krypted2
NFSHomeDirectory: /Users/krypted2
Password: ********
Picture: /Library/User Pictures/Fun/Ying-Yang.png
PrimaryGroupID: 20
RealName: Charles Edge
RecordName: krypted2
RecordType: dsRecTypeStandard:Users
UniqueID: 503
UserShell: /bin/bashNotice that the above is not the whole record you'd typically find with dscl. But if it were, you would not have the AuthenticationAuthority attribute. To see if it can unlock FileVault we can use the -secureTokenStatus operator built into sysadminctl. Simply pass the RecordName and you'll get an indication if it's on or off:
sysadminctl -secureTokenStatus krypted2The response should be as follows:
Secure token is ENABLED for user Charles Edge
To just get the ENABLED response we'll just use awk to grab that position (also note that we have to redirect stderr to stdout): sysadminctl -secureTokenStatus charles.edge 2>&1 | awk '{print$7}'
No clear text password or interactive option was specified (adduser, change/reset password will not allow user to use FDE) !
Creating user record…
Assigning UID: 503
Creating home directory at /Users/krypted2Notice that in the above, the system automatically selected a home directory and UID. We could have passed those as well, using Now let's use dscl to view the user we just created:
Macos Default Admin Password Unlocker
dscl . -read /Users/krypted2
NFSHomeDirectory: /Users/krypted2
Password: ********
Picture: /Library/User Pictures/Fun/Ying-Yang.png
PrimaryGroupID: 20
RealName: Charles Edge
RecordName: krypted2
RecordType: dsRecTypeStandard:Users
UniqueID: 503
UserShell: /bin/bashNotice that the above is not the whole record you'd typically find with dscl. But if it were, you would not have the AuthenticationAuthority attribute. To see if it can unlock FileVault we can use the -secureTokenStatus operator built into sysadminctl. Simply pass the RecordName and you'll get an indication if it's on or off:
sysadminctl -secureTokenStatus krypted2The response should be as follows:
Secure token is ENABLED for user Charles Edge
To just get the ENABLED response we'll just use awk to grab that position (also note that we have to redirect stderr to stdout): sysadminctl -secureTokenStatus charles.edge 2>&1 | awk '{print$7}'
We could append the AuthenticationAuthority attribute with dscl, as we would need a SecureToken. To get a SecureToken, we'll use the -secureTokenOn verb:
sysadminctl -secureTokenOn krypted mysupersecretpasswordTo disable, we'll use -secureTokenOff
sysadminctl -secureTokenOff krypted mysupersecretpasswordGiven that we like to rotate management passwords, we can do so using-resetPasswordFor which takes a username and a password as -newPassword and -passwordHint respectively:
sysadminctl -resetPasswordFor krypted -newPassword newsupersecretpassword -passwordHint 'That was then this is now' Pokemon home screen.
sysadminctl -guestAccount status 2>&1 | awk '{print$5}'
sysadminctl -guestAccount OffYou can also use sysadminctl to do a quick check of the encryption state of the boot volume using the -filesystem option (although there's no on and off verb for this option just yet):
bash-3.2# sysadminctl -filesystem status
2017-12-07 10:37:26.401 sysadminctl[8534:466661] Boot volume CS FDE: NO
2017-12-07 10:37:26.434 sysadminctl[8534:466661] Boot volume APFS FDE: YES
The help page is as follows:Usage: sysadminctl [[interactive] || [-adminUser -adminPassword ]] -deleteUser -oldPassword ] -resetPasswordFor -newPassword ] -addUser ] [-UID ] [-shell ] [-password ] [-home -secureTokenOn -password -guestAccount -afpGuestAccess -smbGuestAccess -automaticTime -filesystem status Pass '-' instead of password in commands above to request prompt.
Why should you switch to sysadminctl for scripts? Entitlements and I'm sure this is how mdmclient will pass management commands in the future… Why should you not? You can't run most of it as root…
